You worked hard to build something. Let us protect it.
Defend your business against phishing, malware, social engineering and ransomware attacks.
Educate, plan, execute, monitor and respond to all cyber security threats, 24/7.
Customizable approach that works best for your
unique security needs.
913-348-4582
Cyber attacks are increasing... and becoming more expensive
The global cost of cybercrime is expected to reach $10.5 trillion annually for 2024, up from $3 trillion in 2015 —a 250% increase in less than 10 years.
of data breaches involved data stored in the cloud in 2023.
80%
$5.13
Million
The average total cost of a ransomware breach is $5.13 million.
100
Million Attacks
The U.S. ranked first in total number of cyber attacks at nearly 100 million.
of SMBs were the target of a cyberattack in 2021.
61%
You deserve peace of mind
Strong password policies, multi-factor authentication, and endpoint protection—these are quick wins that defend against common attacks. From there, find out your specific vulnerabilities and layer on more advanced controls like data backups, employee training, and network monitoring based on your budget and risk exposure.
Watch the video to learn more about the Top 6 Must-Have Security Controls.
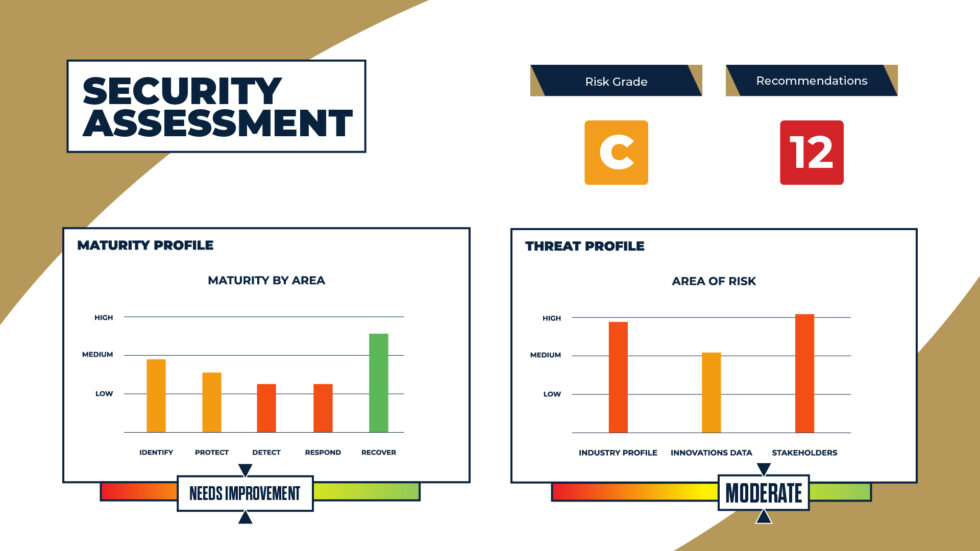
Get a free security assessment
You can’t protect what you don’t know is at risk.
Here’s what to expect from your free checkup:
- Uncover critical security threats.
- Clear plan to fix any vulnerabilities.
- The data-backed report is 100% owned by you.
- Takes less than one hour of your time.
- No technical team necessary.
- It’s free free. Not fake free. You won’t be charged a penny.
Testimonials
Service Areas
Threats you're up against
Phishing
Deceptive emails tricking employees into providing sensitive information.
Software Vulnerabilities
Outdated applications and security patches expose businesses to cyber risks.
Data Breaches
Unauthorized access to confidential data that can lead to identity theft and financial fraud.
Ransomware Attacks
Malicious software that encrypts company data and demands ransom for its release.
Monetary loss of small companies in the United States as a result of cyber breaches as of August 2024
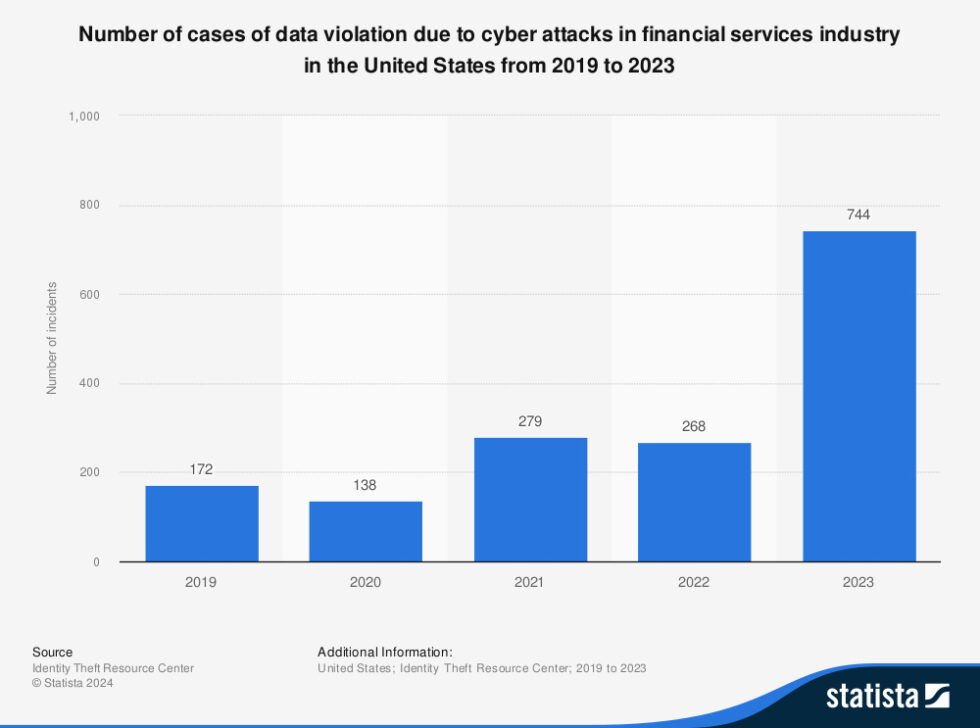
Source
Identity Theft Resource Center
©Statista 2024
Number of cases of data violation due to cyber attacks in financial services industry in the United States from 2019 to 2023
FAQ
Moonshot has a refined approach and a specialized staff to confront evolving threats and communicate risk in plain, business terms. We’ll take the time to efficiently and clearly explain the threats your business is up against and prepare you with high-level defense, awareness and education.
Digital assets are at their highest value and security threats evolve rapidly. In support of your in-house security team, you’ll have access to our specialists’ wide-ranging skillset, strategy, and experience that will make your organization stronger when it comes to data assets and protection.

